Meet with us at RSAC 2025.
Book time

Written by
the Kindo Team
Article
•
6 mins
What is Autonomous Infrastructure?
A Glimpse into Kindo’s Vision
Imagine your cybersecurity setup as a self-driving car, navigating cyber threats on its own. Autonomous infrastructure is like this "self-driving" concept for IT security. It refers to systems that can manage and protect themselves with very little human involvement.
Using tools like automation, artificial intelligence (AI), machine learning (ML), and coordination, these systems can fix themselves, grow as needed, and improve their performance automatically. In simple terms, they can spot problems, solve them, adjust resources, and strengthen defenses on the go.
This idea essentially builds on "autonomic computing," a concept introduced by IBM in 2001. Back then, the goal was to create systems that could set themselves up, fix their own issues, improve performance, and protect themselves without constant human supervision.
Thanks to advances in AI and ML, this vision is becoming a reality today. We now have smart infrastructure that learns from past experiences and gets better over time.
Automated Workflows in Security Operations
An important part of these self-managing systems is security automation, which means setting up processes that automatically deal with threats and routine maintenance.
In the context of cybersecurity, by automating repetitive tasks and incident responses, organizations can make their security operations more efficient and identify threats quicker. Tools like SOAR (security orchestration, automation, and response) work with different security systems to review alerts and take action without needing a person to step in.
This allows tasks like checking logs, isolating harmful software, or sorting alerts to happen in just seconds. Security automation can process huge amounts of data, spot possible threats, and follow pre-set actions – all with little or no human input.
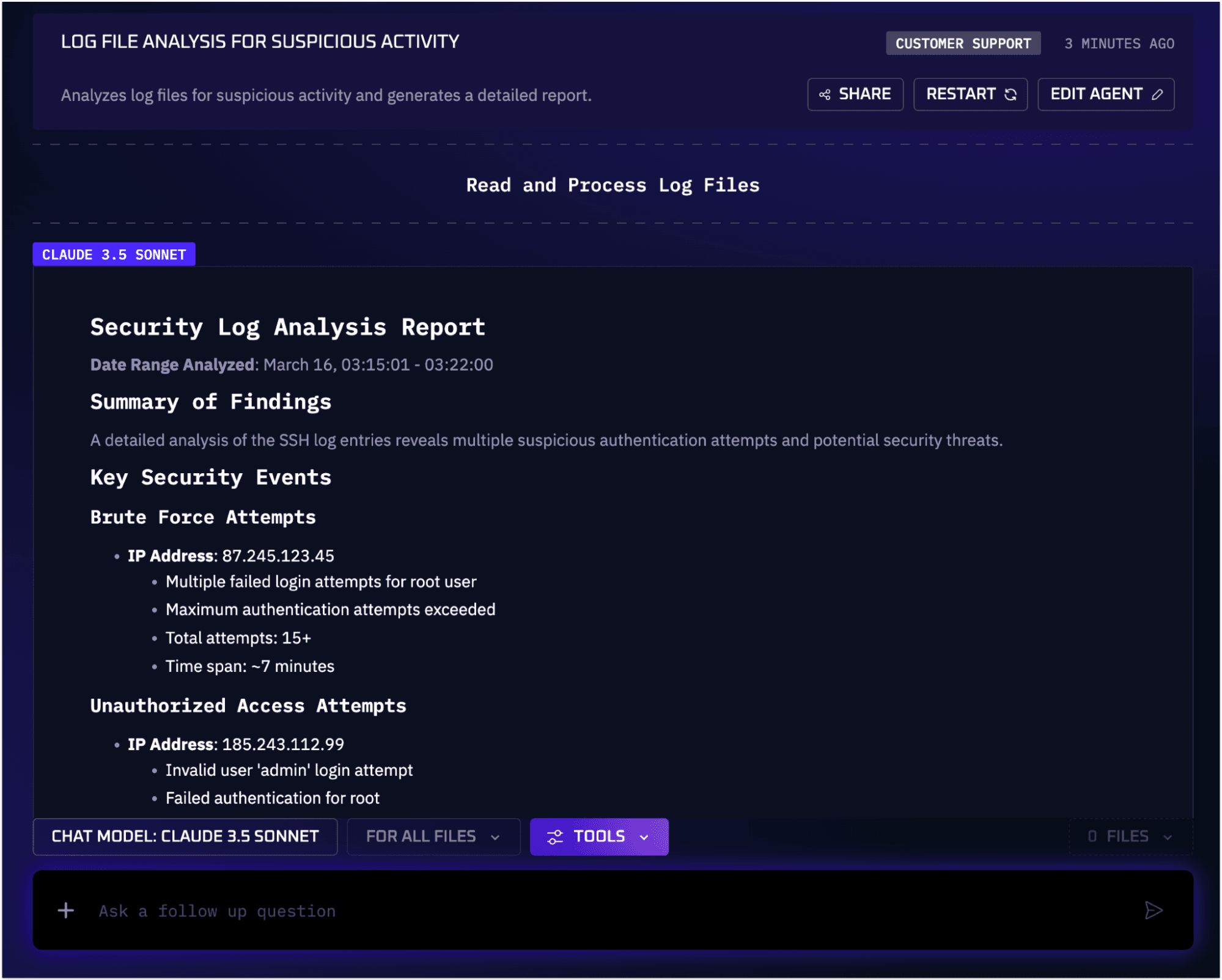
Image: An example workflow that analyzes log files and malicious activity
The result is a more efficient security workflow: incidents are identified and contained faster, and analysts aren’t drowning in low-level alerts. In fact, automating workflows can cut down the manual effort in triaging alerts and reduce human error overall. It provides useful context for identifying and prioritizing threats, ensuring fewer alerts slip through the cracks.
Instead of manually stitching together data from different tools, an analyst can rely on an automated pipeline that gathers threat intelligence, enriches alerts with context, and even initiates remediation steps.
This not only accelerates response times but also allows security teams to focus on higher-value work (like investigating advanced threats or improving security strategy) while the automated system handles the more tedious, grunt work.
Agentic Security: Self-Defending Systems
A key evolution in this automation is what we call agentic security – essentially giving security tools a “mind of their own” to proactively defend systems. Agentic security uses autonomous AI agents that can make decisions and take actions without waiting for human intervention.
Think of it as moving from simple automated scripts to intelligent security guardians that act on alerts independently. These AI agents monitor inputs from various tools (like endpoint detection systems, network monitors, threat intel feeds) and decide in real time how to handle threats.
Unlike traditional automated defenses that follow rigid if-then rules, agentic AI can adapt on the fly. For instance, a standard automation script might detect a malicious file and quarantine it, then stop there until a human checks the system.
An agentic security system, on the other hand, won’t just halt after one action – if it finds malware, it could dynamically launch a deeper investigation across the network or initiate additional countermeasures without pre-scripted instructions. In other words, it behaves a bit like a seasoned security analyst: observing the situation, making independent decisions, and pivoting as needed to contain the threat.
By offloading repetitive and time-sensitive tasks to AI agents, organizations get faster and more consistent responses to incidents. For example, AI agents can automatically triage alerts (filtering out noise), correlate events from multiple sources, and even remediate issues – all in real time. This not only improves threat response speed but also ensures that even a flood of alerts is handled thoroughly.
Kindo’s Latest Launch Debuts at RSAC 2025
Autonomous infrastructure in cybersecurity is a game-changer for protecting and managing systems. By using automation, AI, and orchestration, it creates systems that can fix themselves, grow as needed, and keep improving – essentially becoming self-protecting.
This forward-thinking approach helps organizations stay ahead of threats by acting quickly and intelligently, instead of always responding after an attack. It’s a perfect fit for today’s cyber threats, where attacks happen at machine speed and can overwhelm human teams in a whole range of different areas.
This idea is at the heart of Kindo’s upcoming release at the RSA Conference (RSAC) in late April 2025. Book time with us to demo the latest Kindo launch at RSAC, and let us show you how we can deploy Kindo in self-managed environments.
Want a demo before RSAC? Book a personalized demo today.