

SOC 2 Compliance
Certified & Secure
Earning SOC 2 Type II certification requires rigorous controls across security, availability, and privacy. This certification reflects our dedication to safeguarding sensitive data and maintaining platform reliability.
Continuous Security Assessments
We embrace proactive security testing to identify and address vulnerabilities before they become threats. Partnering with top-tier security firms, we ensure our platform remains resilient against evolving risks.
Third-Party Risk Management
We enforce stringent vendor security standards, ensuring our partners maintain the same level of protection as we do. Every provider undergoes thorough assessments, contractual compliance, and ongoing security reviews.

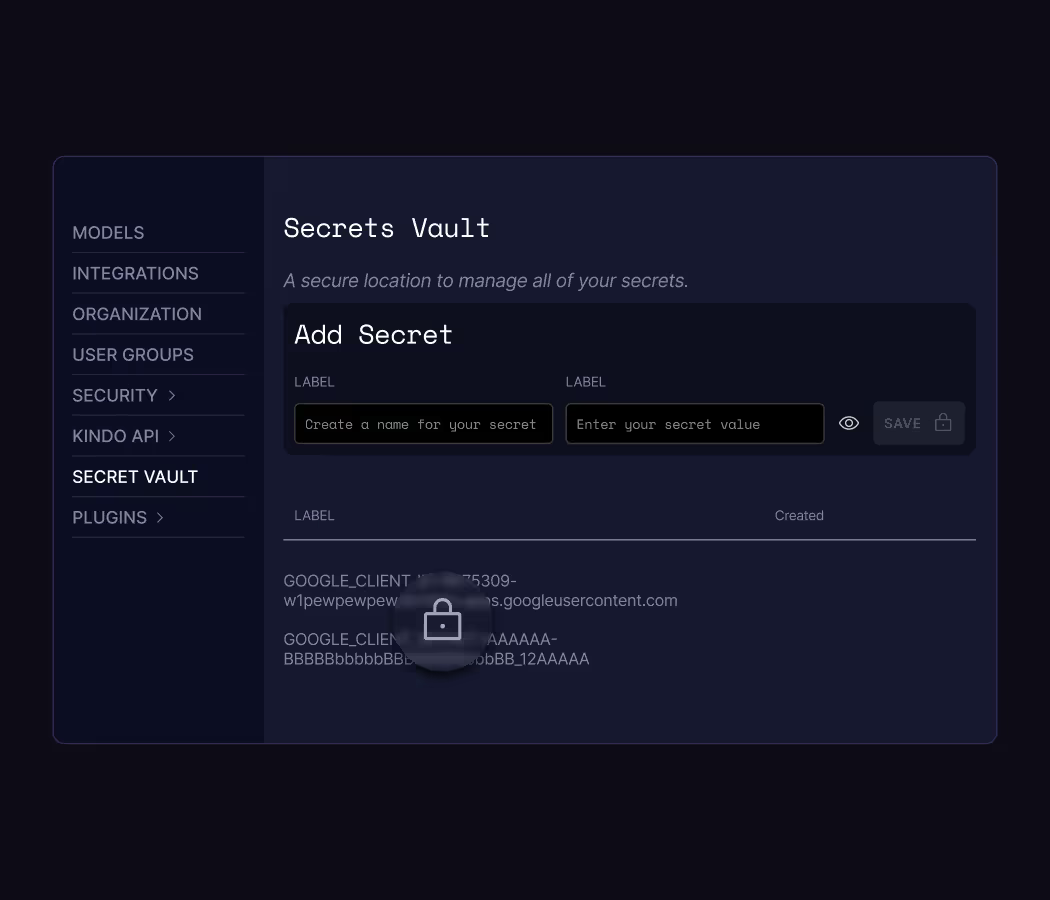
Purpose-Built to Secure AI
Enterprise-Ready Security
Kindo delivers enterprise-grade security tailored for IT and operations teams. Our platform simplifies access control, allowing teams to set granular permissions, share AI models, and enforce Data Loss Prevention (DLP) rules effortlessly.
Protecting Sensitive Information
With built-in encryption and a dedicated secrets manager, Kindo ensures credentials and sensitive data are securely stored and accessed only when needed—without exposing them to unnecessary risks.
AI-Powered Efficiency
Kindo seamlessly integrates with existing tools to automate compliance, reporting, and security workflows. Our AI agents reduce manual effort, freeing teams to focus on high-value tasks.
Enterprise-Ready Infrastructure
Fortified by Design
Kindo is built on a secure, scalable architecture with minimal reliance on external frameworks, ensuring control and reliability for enterprise AI applications.
Layered Defense Strategy
We implement defense-in-depth protections, including real-time threat monitoring, proactive vulnerability management, and disciplined patch deployment to mitigate emerging risks.
Compliance & Governance
Kindo supports enterprise security frameworks like ISO 27001, GDPR, and NIST CSF. Features include Single Sign-On (SSO), Role-Based Access Control (RBAC), audit logging, and data loss prevention to maintain compliance and security integrity.




